Cybersecurity researchers have discovered a new version of HardBit ransomware, named HardBit 4.0, which uses password protection to avoid detection. Unlike previous versions, this variant requires a password to run correctly, making analysis more difficult for security researchers. HardBit, which first appeared in October 2022, is distinguished by the absence of a data leak site, preferring to threaten victims with new attacks to force them to pay.
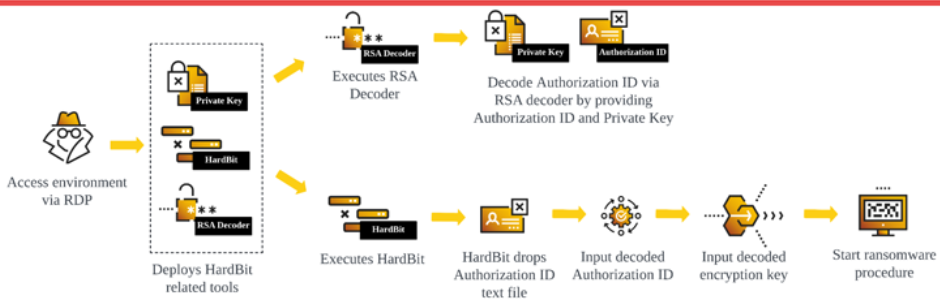
The initial access vector is unclear, but could involve brute force of RDP and SMB services. Once access has been gained, attackers use tools such as Mimikatz for credential theft and lateral movement via RDP. HardBit disables antivirus and Microsoft Defender services, and encrypts files on the infected host. It also offers a wiper mode for permanent file deletion. In 2024, ransomware attacks are on the rise, with strong activity from the LockBit, Akira and BlackSuit groups.
https://thehackernews.com/2024/07/new-hardbit-ransomware-40-uses.html
Credits : The Hacker news
